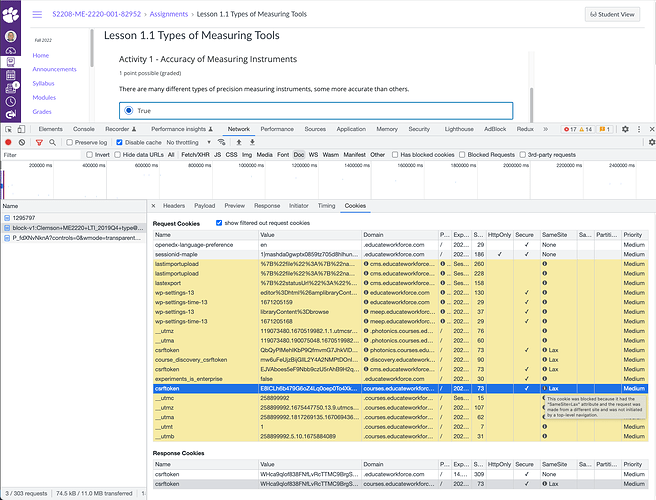
Question for anyone using Django to serve LTI apps for edx.org courses, and thereby using the LTI xblock : have you seen the notice in Chrome about cookies and the SameSite header? If you have the Chrome dev console open when you load an edx.org page that contains an LTI xblock pulling in an external Django app you’ll see something like :
A cookie associated with a cross-site resource at was set without the
SameSiteattribute. A future release of Chrome will only deliver cookies with cross-site requests if they are set withSameSite=NoneandSecure. You can review cookies in developer tools under Application>Storage>Cookies and see more details at and .
If you’ve configured Django’s SESSION_COOKIE_SAMESITE = None, Django doesn’t write SameSite=None , it just doesn’t write anything at all. However, by the looks of this recent pull request in the Django repo, Django is being updated to explicitly write the “None” setting:
Just curious if anyone has thoughts on whether we can assume LTI applications served by Django (with this update) will continue running ok in iframes on edx.org or other Open edX-based sites.
Thanks for your thoughts.
– Daniel
 !
!